
NOTE: this site will be under construction
until I have counted to infinity twice

|
got a virus? |

|
|---|
PC Technician - Viruses and Virus info
|
How to code a boot virus
This virus creates a bat file which is added to the "startup" folder so when the computer boots up the bat file is excuted and creates a gazzilion directories - DO NOT RUN ON YOUR COMPUTER! This does not actually change the boot sector but definitely makes a mess on your desktop. How this file gets into the startup directory by a hacker will be addressed later. |
I have been away for several years and am just getting back to revising this site. Years ago solving the virus invasions was relatively easy ( I am talking about DOS and the earlier versions of Windows ) but today there are so many ways for the hackers to enter your computer it has become scary and mindboggling. I would like to inform you of the various vectors of attack but this would require resources to which I don't have access. So let's get started. From what I understand the boot sector can be compromised, and at first I would have thought this to be impossible. I always thought that a virus which is piece of code which has to be executed by the ( Central Proccessing Unit ) the CPU. By the way the boot sector of a hard drive is in the first track of a HD and is 512 bytes long. So the first thing a computer does ( upon bootup ) is to load this sector into the computer memory and then will execute the code. By the way, the boot sector contains code to point to the essential start up files. So if the boot sector is damaged your computer will not start. In the early years I used a program to edit the boot sector and I could manually fix the code. One trick I used to use was to copy the boot sector to the 2nd sector ( usually empty ) so I would have a backup boot sector. Apparently, there is another type of virus called "root kits" and to me I will refer to anything that invades your computer as a "virus". Anyway, the bat file virus is not really very sophisticated. All you really need to know is how to code a bat file. How the bat file gets into your start folder is a problem which will be addressed later. |
|||
|
Rootkits
This video may be somewhat hard to read - so you can magnify the video using your web browser magnifier ( probably at bottom border of your browser ). I set mine to 200% and then ran the browser at full screen. Or you can use the full screen icon (lower right of video) but runs a little goofy on IE 11. Okay - It was the best of times, and it was the worst of times. This is now my attempt to get Backtrack 5 on the internet and my Local Area Network. I thought this would be relatively easy. Hah! Mr. Bigshot it wasn't. I could not get BT5 to "see" anything - no internet, no Lan. So I embarked on the google merry-go-round. I tried all kinds of "solutions" to no avail. I spent maybe two days trying the google approach. At first I tried setting up BT5 using DHCP and in so doing, I noticed that DHCP assigned an ip address that seemed to be on a subnetwork. Well this is where I wasted a lot time (searhing google to expalin why) so I set the BT5 manually - but still no luck - that is, the manual values where in my LAN but BT5 networking would tell me that 192.168.1.1 ( my gateway on my router) could not be reached (????) - but this is the gateway address of my router. Then I looked at my son's computer (which I built for him about 2 years ago) and opened BT5 and guess what, I could "see" the internet and I could ping computers on my LAN by ip addresses but not by name in the DHCP table. I then looked at his settings in Virtual Box and discovered one setting which was different than mine. To check I highlighted the BT5 selection and then clicked on settings icon on top row of VB which brought up a menu where I selected the "network" choice on the left hand column. I noticed that the network choice was "NAT" and on my computer this was set to one of the other settings (??). So I changed my computer and joy of joys it worked. I could now ping my LAN and an internet site. By the way, NAT stands for "network address translation." It's a tool that many Internet routers use to allow every computer that they serve have its own Internet Protocol address while only using a limited number of actual IP addresses that the entire Internet can see. So I started up X Window on my computer and opened up the Firefox Browser and it all looked fine. To get out of X Window just press "cntl+alt+f1" and then press cntl+c. This will take you back to command mode. I still don't know how to "see" the DHCP table so I can access my other computers on my LAN by computer name. Now I will set up a sacrifical computer to play with, so I can replicate the rootkit video shown above. 
10 of the worst viruses ever Wow - I didn't realize how menacing these attacks have become. We are talking about Billions (with a "B") of dollars as being lost. I just don't know (other than stealing money) why young people would work so hard to do this. I'm missing something here. When I was young all I wanted to do was to chase girls, sports, drink and have fun with my friends, go fishing, not harm anyone. This may sound pretty lame to some of you - but these kids seem to have lost their moral compass. I am completely lost by their insidious and malicious actions, and I am just totally baffled by it all. fig.1 
fig.2 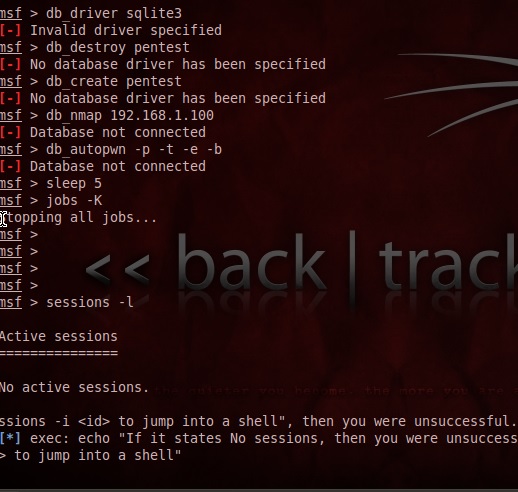
|
The video to your left talks about rootkits. Now this type of infection is one of the most insidious kinds of virus (actually it behaves more like a parasite). Part of the problem is that the virus is invisible to the operating system (e.g. Windows) making it very hard to detect. The hacker can design it with malicious code that can almost do anything which includes installing a keylogger program which captures keystokes and sends this info back to the hacker. This info may contain your name, SS number, credit card number, passwords, etc.. I wish I had a deep understanding of the rootkit - then I would have it return a time bomb to the hacker to destroy his/her computer - like erase his hard drive. I will attempt to figure all this out in the future. By the way the boot sector must contain a two byte signiture (0x55 and 0xAA) and if is missing or corrupt - the computer will not boot. There is some hope to stopping rootkits and that is an improved BIOS which will prevent any modifications to the first sector of the hard drive. By the way the presenter uses a program called "back track 5" it is for linux machines but I found a link HERE which will allow you to run backtrack on windows. I'll get back to you soon. If you have Linux instead of windows then obviously select the Linux distributions. I am back, with 3 of my nine lives lost forever. And here is what to do next. 1. Download VirtualBox 5.2.8 from the virtual box site given above and click download button, on next screen choose host, in my case I selected "windows hosts". You should click on run to install this package. Just click on through with the defaults.The install program may put on the task bar (flashing) and open it and click your approval to continue. Eventualy you will then click finish ( click on the after install box to also start up VirtualBox (VB) ). Also download the Virtual Box Extension Pack as you may need it. Save this file to your hard drive. 2. Now that you have VB running you will need to get the Backtrack program HERE as an iso file and download it. Rmember to select the correct verision to match your computer i.e. 32 bit or 64 bit. You also have a choice between KDE and GNOME - these are the graphical interface if you run X Window. I downloaded both KDE and Gnome and put mine into a folder (I called it vms) on the C: drive. So now you have to save the download Backtrack and save it into the folder "vms". This way I can have 2 graphical versions which are stored in the "vms" folder on my hardrive. Now go to VB and click on new button and name the virtual machine "backtrack" (in my case I named them backtrack-KDE and backtrack-GNOME ). Now select a type and a version. I picked "other" and "other/ unknown". Now select a memory size (ram), I selected a value in the green area - if you make it too big you will take away too much memory from the host system ( i.e. Windows ), and will give problems when VB tries to run. On the next screen choose "create a virtual hard disk" and click create. Now select a hard disk file type - I selected VDI - then click next. The next screen I choose "Dynamically allocate" then next,I gave a file size of 10 GB. and clicked "create". At this point the VB should show your virtual disk. Now click on green arrow start button. A window should open and you have to give the host (the .iso file) drive. Remember I put this file into the "vms" folder and you will click on the tiny folder to navigate to your iso file. Click on open and you should see the name of the iso file in the box. Then click start. Backtrack should start and it does on my son's computer but on my computer it only shows the backtrack logo and a lot of gibberish but then I got a prompt which took a while. The prompt looks like this "root@bt: # ". I then typed in ifconfig and it showed me the results of this command (see left hand side). I then decided to download an iso file for a version of Ubuntu and added this to my virtual machine so now I would have both Backtrack and Ubuntu available (just like my son's computer). But, lo and behold the virtual Ubuntu doesn't work and I will get back soon with (hopefully ) a solution as you may get a similar problem. Oh by the way, it dawned on me that BackTrack is just a process running in a Linux enironment. I used to know command prompt mode for unix(linux) but that was many many years ago. I will try to catch up with this former knowledge.
See you soon, that is, if I don't slit my throat.
Well I am back, I think the problem with getting the Ubuntu linux to run on my computer is
because I don't have enough memory (3 GB) but it runs on my son's machine because he has
8 GB of memory. So, I am stuck because I really can't allocate more memory as it would slow
my Windows environment. I got a new computer ( a laptop with 8 GB of memory ) and will
see if Ubuntu will run on it. I'll let you know.
But, first I would like to talk about the rootkit virus. The fisrt thing we should look
at is how a computer works at the microchip level i.e., the CPU. Then we can look at how
a rootkit works to exploit what is called a buffer overflow attack. You can read all about
it HERE. Or, I will try to give a less detailed analysis (I hope), as my last encounter with assembly language was over 40 years ago when I wrote code for the 8087 cpu - the co-processor
for the 8088 chip. The 8087 chip was a floating point processor.Anyway, the CPU is composed of
three main parts; the Control Unit (controls the input/output devices),The arithmetic Logic Unit,
and the Immediate Access Store ( the memory available for programs and data ). This last unit
use what is called resgisters to load your program into RAM memory. There are 8 registers in a
X86 Processor which allows your program to build 6 segments which are stored in memory from
high memory to low memory. the top segment is called the "Stack" and the last segment is
called the program (and data) code. In a X86 processor the three registers that we will be
concerned with are the ESP, EBP and EIP. The ESP regiser (Extended Stack Pointer ) marks the
top of the Stack. The EBP ( Extended Base Pointer) which points to base of the Stack. And
the EIP (Extended Instruction Pointer) which points to the address of the next instruction of
your code to be executed. This register always points to an address in the "Program Code"
memory. The stack is configured as a LIFO (Last in First out) data structure. So,
smarty pants what does all this mean. If you execute code that pushes an address onto
the stack, called "push" in assembly language it is placed at the top. If you perform three
push commands like push 1, push 2, push 3, then when you want to retrieve these values then
your code could say pop, pop, pop, (to retrieve 3 addresses from the stack - assembly command) which means you want to retrieve the addresses 3 successive times, then the addresses would be returned in reverse order - 3,2,1.
So now let's get into exploiting the Buffer Overflow. It seems there are 3 ways that stand between
you and a successful buffer overflow attack. If you don't know where the EIP is located then you
cannot construct an attack. The second problem is finding out the ESP address and this is difficult
because this value is constantly changing and can be captured only when a buffer overflow happens.
The first problem is resolved easily ( oh yeah - easy for you - difficult for me). The second
problem is a lot more difficult as it involves the use of a Disassembler/Debugger.
One such program is called Immunity. You can use a language such as python to write a pycommand
for Immunity. A second method uses pydbg ( python debugger library ) to analyze an exception
condition and print the register values. (What???). The third problem is difficult and tedious.
The main idea is to send a string of characters from (0x00 to 0xff) and to use pydbg and monitor
the results. When a bad character is encounted e.g. a line feed, a carriage return, etc. the target
progam will stop just before the bad charater. You continue to do this until all bad characters
are found. This is tedium epitomized.
One last item, you have to know a priori which applications have a buffer flow vulnerabilty.
You would need a disassembler to look for functions known for their vulnerability.
The use of fuzzers ( whatever this is) to cause the target applicaion to crash and then
analyze the results ( Yeah sure ! ). Okay enough of this now we will examine an example
of exploitation. You can find this HERE
I am not going to give a summary for this as it involves downloading of tools to help you.
---> to be continued
Back again. I carefully followed the Rootkit video above and finally caught on what he was
trying to do. The first part he was just demonstrating that his sacrifical computer (Windows XP)
with a plain vanilla OS. So he opened MS (Sysinternals) and ran a program which I tought was
a rootkit (the bad guy) but instead it was a Rookit Cleanser. My Sysinternals suite did not
show this program. By the way the Rootkit Cleanser is no longer used - it has been replaced by
a newer version (look for it on google). His cleanser was started and didn't find any rootkits
as it shouldn't with newly setup XP computer. So he wanted to double check and he downloaded
a copy Of BlackLight to make sure. Both these programs showed no problems. Now for the exploit
part. When looking at his video and Backtrack 5 - I saw two icons on the left side which were the
actual rootkit viruses - he was planning to use to upload to the target machine. I am not sure
where he got them as I tried to download these but haven't found them yet - so I will continue
to look for them (not important to me as all I want to do is gain entrance to one of my
computers on my network). Anyway, the next step is to use the nmap program which reveals
all active ip addresses (over a range of 20 nodes) on his network (local LAN). He found two open computers
which includes his XP machine. So this will be his target machine (192.168.159.136).
I tried to run nmap with the same options as his, but my nmap program objected to the
the -T5 option (as his video was made in 2012). Now I had to read all about nmap - UGH!
I would rather watch grass grow instead. Now we can now run a program which will search out
every port (for a given ip address - in this case 192.168.59,136) that is open for
a vulnerablity attack. This uses every type of brute force method to make this determination.
By the way the program is in the directory /pentest/exploits/fasttrack and is called
fast-track.py. if you are in the fasttrack directory you can execute the program (obviously
a python program) by typing ./fast-track.py -i (note the ./ in front of the name ). Well I tried
this with no luck. This program starts an interactive session with a prompt of
msf - and I just happened to notice that the database it required can't be found - while
the rootkit author shows a DB of "postgresql" and my session shows that the DB is
called sqlite3. So if the DB can't be found this is not going to work. Actually, these
two DB I described above are (to be precise) database drivers. Now I have to track down
two things - which driver is needed and how to insert it into fast-track.py. So back
to the google merry-go-round, with gallantry and intrepidity. --> to be continued.
Back again. Now ready to make an attack on my network. Now execute /pentest/exploits/fasttrack/fast-track.py -i
and you should get the screen shot in fig. 1 (see left hand side). Select option 2 . The next screen should
prompt you with some piggy-back commands in Metasploit. Note: you can select a single ip address of
the target or a range of ip's to search all computers on
your LAN. I used a single ip address, because if you select a range this will take a really long time. I then typed
in a single argument (eg) -PN 192.168.1.100 and got a prompt to select either Bind or Reverse. I selected number 1
but got a message that there was no active or invalid driver specified (see fig.2). So obviously, this was not going to work.
By the way fasttrack program spawned another proccess called msf (a forked child process) which then said that all
jobs were stopped. Now what? I then took a guess that maybe if I just started the msf process by itself I could enter
the commands manually. I did try the suggested fixes but this just dragged me down a sinkhole as you need to get all
dependencies for this to work. So I started "msfconsole" which took me to the msf> prompt but first stop the fast-track.py
program with "quit" and number "12" to completly exit fast-track. Once msfconsole started I got the msf> prompt.
Now type in "db_driver". It now displays the active driver, mine was postgresql. Now type in "db_driver postgresql".
You should get message "using database driver postgresql". Now type in
Continued on page 2
|
|||
 |
|





